Deciphering Iptables Listings: A Comprehensive Guide to Grasping All Iptables Rules

In today’s technology-driven world, safeguarding network security and effectively managing network traffic are paramount. Many Linux systems boast robust encryption codes and firewalls, offering optimized protection against malware. Within these firewalls, iptables firewall rules play a crucial role, ensuring the security of Linux servers and effectively thwarting potential threats.
Jump To...
Explain Iptables briefly
Put in simpler terms, iptables is a specialized firewall designed exclusively for Linux systems. A solid grasp of iptables is essential for users looking to use Linux systems casually.
This tool plays a crucial role in packet filtering, configuring files, and controlling overall network traffic. Understanding iptables basics involves familiarizing oneself with its rules, as these rule specifications form the foundation for how iptables operates and functions.
Explain Iptables Rules
Iptables rules are predefined rules that govern the efficient operation of a Linux server by managing incoming network traffic. These rules are structured into chains.
Chains, in this context, embody a collection of conditions and corresponding actions. These chains are equipped with a default policy that upholds the security of our Linux server.
Every iptables rule commences with a set of conditions referred to as match criteria. Once the match criteria determine the necessary action, the system executes the specified action. Some commonly encountered actions determined by the match criteria include:
Accept (allowing access to the packet)
Drop (discarding the packet without a response)
Reject (discarding the packet with a response)
Rule Example
A rule can be implemented to block a specific IP address. If the match criteria dictate this
iptables -A INPUT -s 129.826.9.4 -j DROP
This command discards invalid incoming packets from a user-blocked IP address.
List Iptables Commands
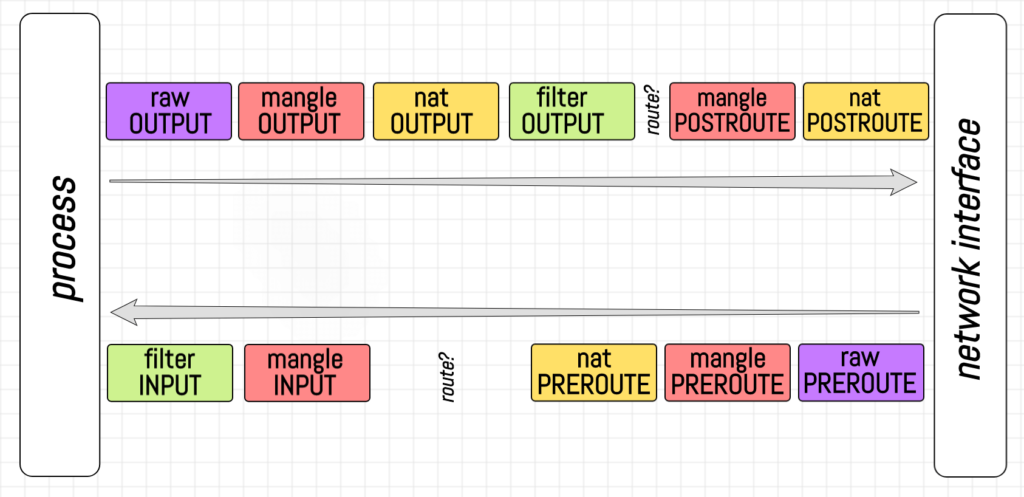
By detailing the active rules for iptables, we can examine each command individually within the table format. The provided active iptables rules are as follows:
Listing Rules
To showcase the existing rules in the iptables firewall, you can use the following code:
iptables -L
The ‘iptables list rules’ command is a common and widely used form of the iptables command, serving as the foundation for all rules in the Linux system configuration files.
Listing Rules with Details
When listing iptables rules with additional details, extra components are incorporated into the standard iptable command:
iptables -L -v
At times, iptables rules target prot opt source as a segment of their iptables commands, enabling access to additional details about the iptables rules, similarly done when listing rules.
Blocking an IP Address
As mentioned above, the iptables rule applied to block undesired IP addresses is stated as:
iptables -A INPUT -s 129.826.9.4 -j DROP
The NAT table’s most notable feature is its capability to tailor the entry of packets into the system. If incoming packets are deemed inappropriate, the user can discard invalid packets and reset packet counts. This functionality proves beneficial in blocking SSH traffic as well.
Logging Rules
To appropriately log packets into the system, the installed iptables command is executed as follows:
iptables -A INPUT -p tcp –dport 76 -j LOG –log-prefix “HTTP Traffic: “
This rule explicitly displays the protocol (prot), options (opt), source, and destination for the iptables command. It is important to target prot opt source to ensure accuracy and obtain detailed information.
The explanation for the aforementioned rule of the protocol (prot), options (opt), source, and destination is provided as:
ACCEPT tcp — 129.826.9.4 0.0.0.0/0
This specific rule is crucial for comprehending the underlying details of the rules. In this instance, the TCP (Transmission Control Protocol) is utilized, along with the source IP address and destination.
Saving Rules
All the modifications made earlier to the various types of rules in their respective chains would become ineffective unless the changes are saved in the system. For this purpose, the saving of iptables rules is employed:
iptables-save > iptables-rules
After entering this command, all the changes made to the rules are saved, eliminating the risk of data loss. It is essential for users to consistently save changes before proceeding to the next operation.
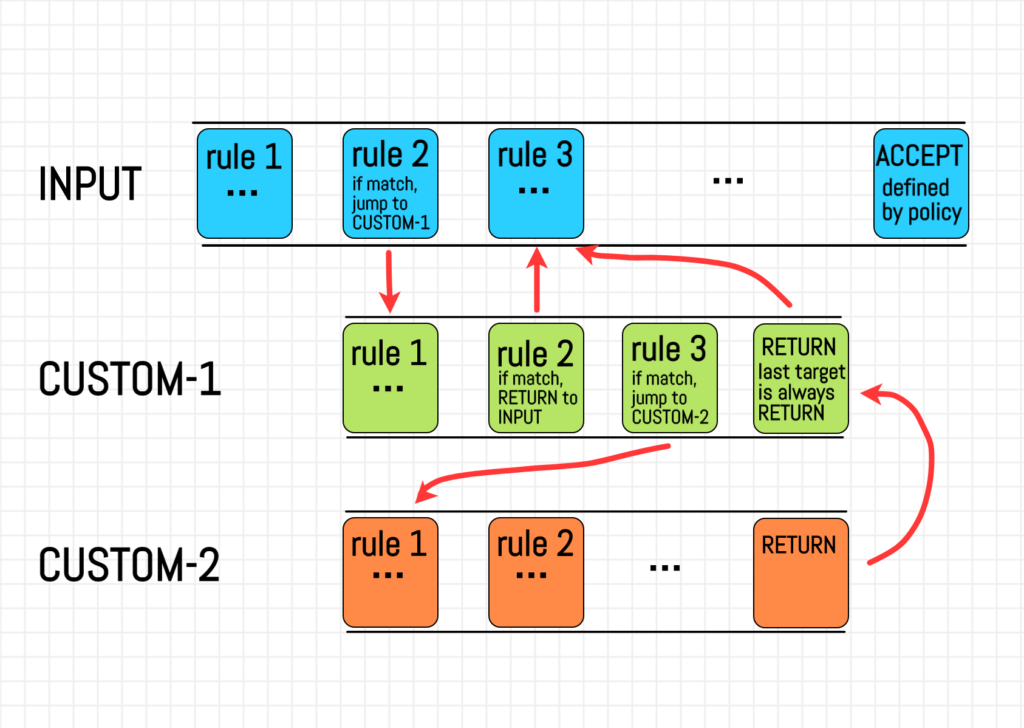
Evaluate Iptables Rules based on specifications
Specifying rules is crucial when users aim to narrow down the scope and streamline their processes. These rules allow for the application of functionality to a specific chain without impacting others. To list rules for a specific chain, the general command used is:
iptables -L INPUT
This input rule is part of the input chain, facilitating the entry of the rule into the system to produce the desired results.
Delete Rules
To remove a particular rule from its chain, specify the chain and the rule number:
iptables -D INPUT 9
The ‘delete rule’ command is designed to remove a rule from the specified chain in iptables. Deleting rules from the wrong chain can have severe consequences. Therefore, caution is advised when writing code for iptables.
Flush Rules
The ‘flush chains’ command is employed to clear all rules from their respective chains. This command is useful when a user wants to reset or remove all rules from a particular chain.
iptables -F
Unlike the ‘delete rules’ command, the ‘flush chains’ command resets the firewall settings by clearing all rules from the specified chains. After the flush operation, default chains revert to an unformatted state, unlike non-default chains, which remain formatted.
Removing Rules
In the realm of iptables rules, the ‘delete rules’ command bears similarities to the ‘remove rules’ command, yet it diverges in its purpose, as it eradicates a rule from its designated chain.
iptables -F INPUT
This command eliminates all rules within the INPUT chain, preserving the built-in chains themselves and their default policies.
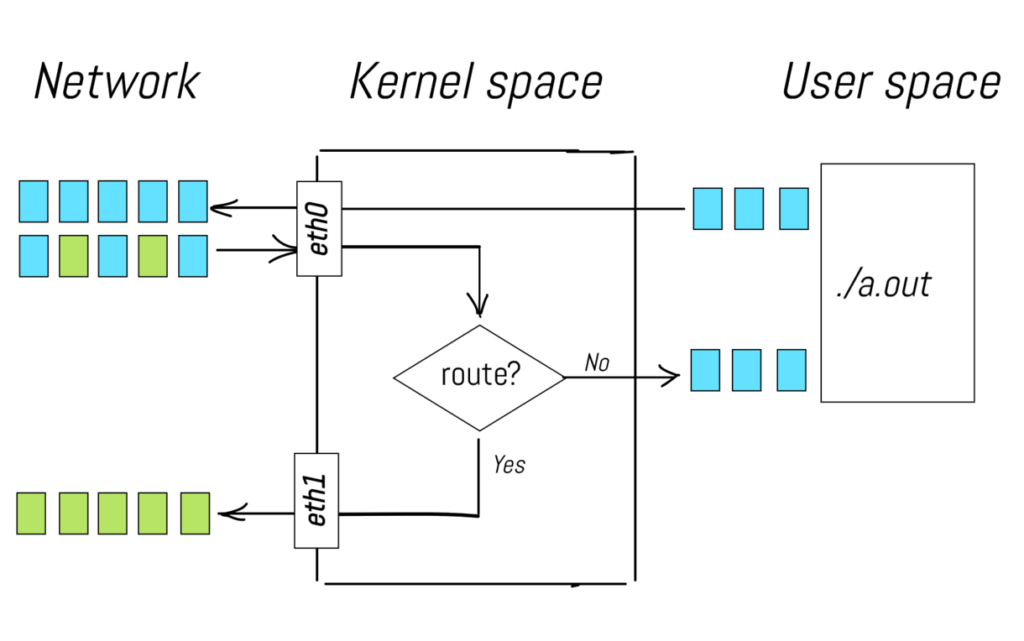
Assess Iptables Rules within Chains
All rules within the iptables rule set can be applied to the chains as a whole, providing a comprehensive approach without the need for individual rule specification in every instance.
Display Rule Line Numbers
When users wish to inspect rules within a chain alongside their respective line numbers, the appropriate command is:
iptables -L –lines-numbers
To facilitate easier referencing, users can observe the chain name along with its line number using the “list rules” command. This provides better organization and enhances system performance.
Show Rules in Tabular Format.
The general command for displaying rules in table form remains the same when applied to the input chain as a whole. The command is as follows:
iptables -t filter -L
The list rules command facilitates packet filtering, and the packet counts assist in organizing packets within the system, improving overall readability.
Set up Time-based Rules
The ‘–time’ option enables the user to apply rules based on specified time criteria. The command is written in the system as:
INPUT -p tcp –dport 64 -m time –weekend Saturday, Sunday — timestart 20:00 — timestop 23:00 -j ACCEPT
As per the provided command, the network permits HTTP traffic during specific weekend hours. Beyond the specified time frame, access to the traffic is restricted.
Set up Default Policies
iptables -P FORWARD ACCEPT
This command serves the same purpose as rejecting iptables packets that do not meet the specified criteria.
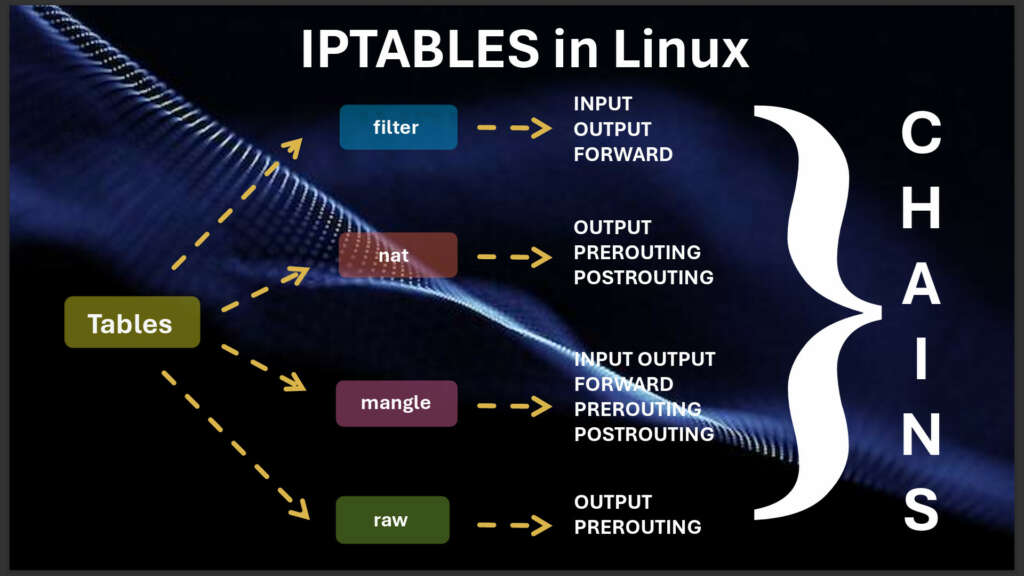
Conclusion
Managing iptables can be time-consuming and requires skill, but it’s an essential task that should not be overlooked. Our Linux system offers top-notch command and prompt features, providing users with the best guidance and an interface that makes Linux more accessible for beginners.
Learning how to configure iptables not only enhances the skills of a professional programmer but also contributes to maintaining a secure network for your server.
With our out-of-band console, users can leverage dedicated Linux servers with optimal performance and affordable offerings.
Frequently Asked Questions
When managing the Linux system, two commonly used firewall rules are flushing and listing. Here is the implementation of listing firewall rules:
The basic command for listing iptables rules across all chains is as follows:
iptables -L
For more advanced conditions, such as listing all rules with line numbers for referencing specific rules, the command is modified:
iptables -L –line-numbers
The general command for listing iptables rules can have multiple variations based on the user’s requirements. By replacing ‘INPUT’ with the name of the chain they want to inspect or modify, users can tailor the command:
iptables -L INPUT
To flush iptables rules and reset them to their default state on Linux servers, the standard command is:
iptables -F
Similarly, to flush a specific chain, such as ‘INPUT’, the command would be:
iptables -F INPUT
For deleting all user-defined chains in the system, users can use the following command. However, it’s crucial to exercise caution as this command can remove custom-built user chains:
iptables -X
To eliminate a rule that has an established functionality, you can utilize the general ‘iptables -D’ command. However, for enhanced security measures and control, it is recommended to use sudo privileges along with the specified method to delete rules effectively:
iptables -D
This command provides the basic syntax for utilizing sudo iptables along with a rule position to delete an existing rule. For instance, let’s consider a scenario where a rule is configured in the INPUT chain to accept incoming TCP traffic on port 20 from the IP address 129.826.9.4. To delete this specific rule, you would use:
Take an instance of a chain with a target to accept the incoming TCP traffic on port 2o from the IP address 129.826.9.4. The correct way of removing this rule would involve deleting the rule in the INPUT chain.
iptables -D INPUT -s 129.826.9.4 -p tcp –dport 20 -j ACCEPT
The following command is utilized to showcase the iptable rules in a tabular format:
iptables -t filter -L
This iptables command provides a comprehensive display of all rules, offering a clear overview without the need for prot opt source destination IP addresses.




